Medical device manufacturers must follow various regulations for their fielded devices, generally referred to as postmarket requirements, which include tracking and reporting malfunctions and injuries. Most have formal procedures and processes in place to satisfy these requirements. However, security incidents impact medical device manufacturers, and their customers, in ways that go beyond the requirements satisfied by existing procedures.
Effective response to security incidents requires preparedness. Attempting to pull together a team of responders and weave together disparate processes under the extreme pressure of a security breach is nearly impossible. An organization might be successful using ad-hoc methods, but it’s not a sustainable strategy as threat vectors continue to grow with every newly discovered exploitable vulnerability. In times of extreme crises, having a planned response can mean the difference between life and death. In terms of security incidents in healthcare, having a planned response can reduce the overall cost to medical device manufacturers. “An organization’s ability to respond effectively after a data breach is strengthened by the presence of an incident response (IR) team that follows and incident response plan…the formation of an IR team and testing the IR plan mitigate data breach costs more than any single security process.”1
The development of an incident response (IR) plan should be a top priority for medical device manufacturers. Equally important, however, is the continuous maintenance of the developed plan. This is just the nature of the continuous evolution of medical device cybersecurity and typical organizational change. Threats evolve, bad actors discover new exploits, product profiles change, people leave and join the organization, and before you know it, the original incident response plan is woefully out of date.
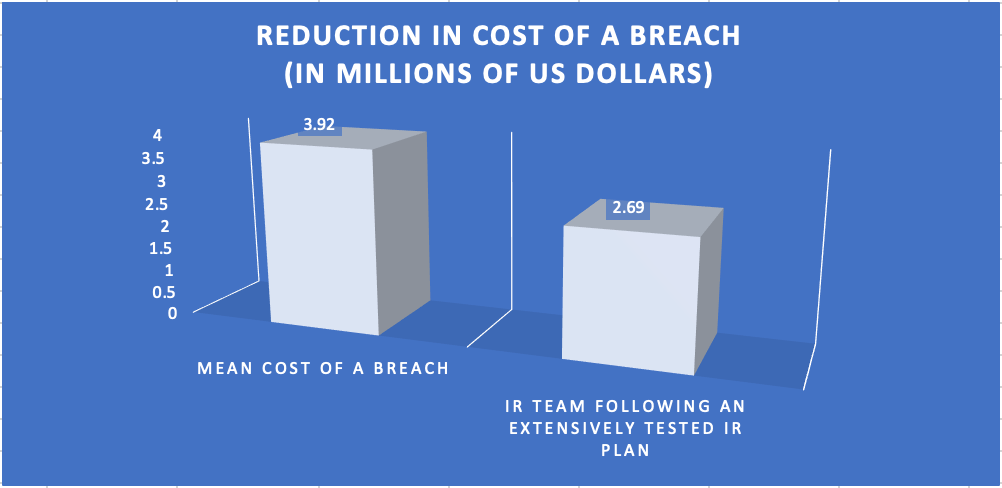
One of the most effective methods of maintaining an IR plan is periodic testing by a formal IR team. In the Ponemon study referenced above, the mean cost of a breach was $3.92 million US dollars. Organizations with formal IR teams following extensive testing of IR plans effectively reduced that mean cost to around $2.69 million US dollars, saving $1.23 million US dollars. This is significant, especially when considering the fairly modest cost of developing of an incident response plan.
Of course, all medical device manufacturers have financial and resource constraints, and in some cases, it might be difficult to carve out the money or the time to develop an IR plan, form an IR team and apply resources to continuous testing. There are several IR plan templates available, some freely downloadable and others with some restrictions, however, the process does not need to be overly complex or overly expensive. As a matter of fact, with proper scoping, medical device manufacturers can get started quickly, develop a plan, form a team and put some tabletop exercises in place.
For specifics on developing and maintaining an IR plan, see our article titled “Developing an Incident Response Plan for Medical Device Manufacturers”.
Ken Zalevsky
CEO, Vigilant Ops
Former Head of Medical Device Cybersecurity, Bayer
- 2019 Cost of a Data Breach Report. Ponemon Institute.
IBM Security, (https://doi.org/IBM Security).


